
Did you know that the most common way that cybercriminals gain access to company systems is through user login details?
Sometimes they’re leaked online, sometimes they’re guessed, sometimes team members unknowingly pass their login details along to someone they think they can trust, only to find that their mailbox has been compromised.
How cybercriminals gain access to the details is less important than what they do once they have them. They’re able to access a business’ critical data, manipulate it, or hold it ransom. They are able to garner further details by posing as a legitimate team member, requesting information from their ‘colleagues’.
Even the strongest passwords can become compromised, which is why having a single password isn’t enough in this modern age. What you need is Multi-Factor Authentication, or MFA. But what is it, and how can it keep your business’ critical information secure?
What is Multi-Factor Authentication?
Our clients often ask us, “What is MFA authentication, and do I need it for my business?”
Multi-Factor Authentication (also known as Two-Factor Authentication) is a type of Advanced Threat Protection that uses a variety of methods to login to a system. Rather than just having a single password to access information, MFA lets you use multiple authentication methods to ensure that the right person is gaining access. This kind of Identity & Access Management means that even if a cybercriminal gains access to your password, there will be an extra level of security stopping them from accessing your systems.
MFA is so easy to implement and adds so much value to any business’ security processes, that we always recommend putting it in place.
What Types of Multi-Factor Authentication Are There?
Now that we’ve answered the question of “What is multi-factor authentication”, you may be wondering what types of authentication you could be using.
The types of MFA are often split into three categories: What You Know, What You Have and Who You Are.
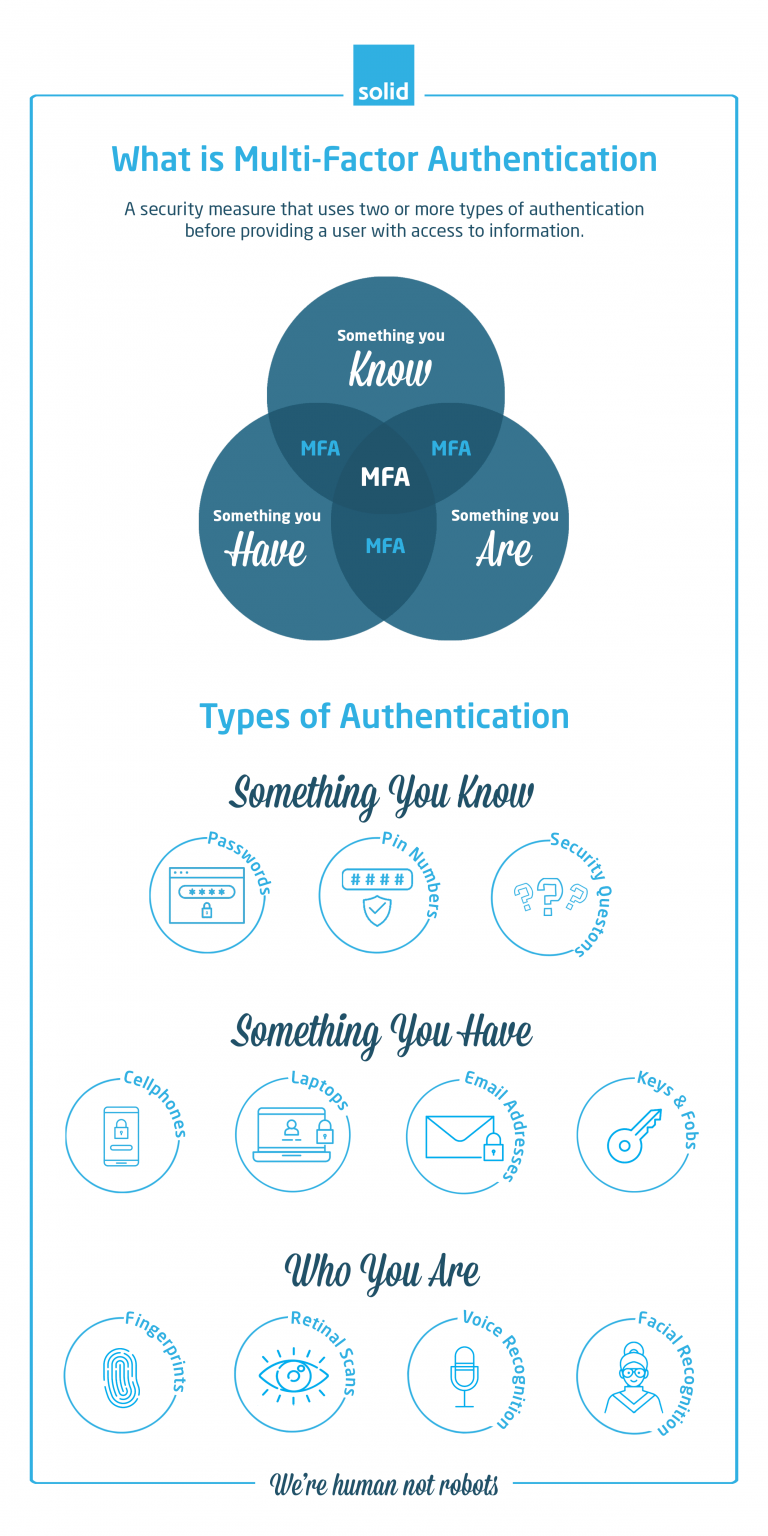
- What You Know
Information-based authenticators are based on the knowledge that you have. These can include passwords, pin numbers, security questions, or any combination of the three.The biggest difficulty with knowledge, is that it is often easily gained. Passwords and pin codes can be leaked or guessed, and standard security questions, such as asking for a mother’s maiden name or a pet’s name, are often easily deduced thanks to platforms like social media. While using information as an authentication is a popular method of email security, for example, it is ineffective on its own.
- What You Have
Devices can be great authenticators. Though cybercriminals may gain access to information, it is rarer that they will gain access to a user’s laptop, cellphone, key or fob. Whenever a user tries to log in, MFA will allow the site to send a separate pin number or code to a specific device or email address. Without the additional password or pin number, the user won’t gain access to the platform.And while physical keys and fobs may not be particularly useful when it comes to online access, they can be used on-premises as an additional layer of protection for any property not stored online.
But, while devices are certainly more secure than information, they can still be at risk, especially as devices like computers, laptops and cellphones will often have password managers on them. This means that if a device gets stolen, criminals suddenly have potential access to a wide range of platforms.
- Who You Are
The most secure methods of authentication are directly tied to you as a person – your fingerprints, your voice, facial recognition and even retinal scans. By using these security techniques, you severely limit the access that a cybercriminal can gain, since you would need to be physically with them in order for them to access information.This being said, there are plenty of movies (and real life situations) out there that show the lengths to which criminals are willing to go to gain access to critical data. This is why, even when you are using the most secure of the authentication methods, using MFA is essential as an additional measure to keep your company’s information and systems protected.
Is Multi-Factor Authentication Right For Your Business?
We’ve answered the question of “What is Multi-Factor Authentication”, and now you may be wondering if it’s the right security solution for you.
The answer is yes.
There is not a company out there that could not benefit from Multi-Factor Authentication, and setting it up for your business is simple. If you’re ready to jump straight in, scan the QR code below and get started right away.

If you want to chat through the benefits of MFA and how it could be helping your business, it’s good to have an IT company in South Africa that you can trust to have your best interests at heart. Get in touch with Solid Systems today to start putting your company’s security first.





