
The landscape of network security for businesses has changed exponentially in recent years, driven by the increasing amount of data that companies are collecting, processing, managing and storing, the way that cyber threats have been evolving, and the adoption of remote and hybrid work environments. Protecting your business’ digital assets has never been more important, or more difficult to achieve.
In 2024, it’s critical for small and medium enterprises (SMEs) to focus their efforts on improving their network security. But what steps should you be taking, what are the risks that you should be focusing on protecting yourself from, and who can you trust to help you make the right decisions for your company?
In this definitive guide, we’ll explore the essential components of a robust security strategy that will safeguard your business now and into the future. We’ll discuss why network security is more important than ever, outline the evolving risks facing businesses, and even give you a comprehensive network security checklist to ensure your systems are secure from the latest threats.
What Is Network Security?
Let’s start off with the basics. Network security is all about securing your business’ infrastructure – your hardware, software, cloud services, servers and more – against intrusions, corruption, or unauthorised access. To do this involves putting measures, policies, and procedures in place to prevent and monitor for breaches that can come from a variety of sources, some of which may be malicious, and some of which may be accidental.
From simple firewalls to the most cutting-edge AI-driven threat detection systems, network security encompasses a broad range of tools and strategies to keep your data safe and your business out of harm’s way.
Why Is Network Security More Important Than Ever?
There can be no denying it – cyberattacks are on the rise. Every day we hear about new threats that are emerging, new attacks that have crippled businesses, and new techniques that attackers are using to gain more access to company data. It’s no wonder that network security importance has been focus for businesses around the world over the last few years.
On top of the rising number of attacks, the interconnectedness of the modern business world means that a single security breach can have catastrophic effects. And I’m not just talking about the financial implications of paying off a ransomware attacker or having to recover your data from a leak. I’m not even talking about the fines that you might have to pay under South Africa’s POPI Act or the EU’s GDPR if personal information becomes compromised. There’s also the massive damage that an attack can do to your reputation and the trust that your clients place in you.
And then there’s the fact that work environments are expanding. A few short years ago, you only needed to protect your office environment, ensuring that the devices in your office could connect to relevant resources and barring your network from any outside access. But with the COVID-induced lockdowns of 2020, businesses started finding themselves needing to accommodate remote workers, or facing closure. While remote work prior to 2020 wasn’t unheard of, working from home or hybrid working have almost become the norm since then. And both scenarios pose challenges to network security, as your business needs to adapt to track outside access attempts more closely, and secure more devices than ever before.
With an increasing number of devices being added to business networks, from employee smartphones to IoT devices, each node acts as a potential entry point for cybercriminals. Network security is the last line of defence between your business and those who would do it harm, making it a vital investment for the health and future of your company.
What Network Security Risks Are Businesses Facing In 2024?
The world of network security threats is constantly evolving. What was considered best practice to protect your business and its data a year ago may no longer be enough today. Some of the most pressing security risks facing businesses in 2024 include:
• Cyber Threats
When we talk about threats to your business, cyberattacks are likely the first risk that comes to mind. And there’s a reason for that. Attacks can take many forms, from ransomware that encrypts your data and demands a payment for its release, to Distributed Denial-of-Service (DDoS) attacks that overwhelm your network, effectively shutting it down, to phishing attacks that see the humans in your business clicking on seemingly innocuous links and accidentally downloading malware that gives attackers access to your systems. There are social engineering attacks that see cybercriminals posing as people you trust, and zero-day exploits which see them taking advantage of newly-found software vulnerabilities before the developers have even had a chance to recognise the risk and release a patch. Cyber threats are evolving at a rapid pace, making them one of the biggest risks to your network security.
• Software And Hardware Vulnerabilities
No software or hardware is immune to vulnerabilities, and as new weaknesses are discovered, they present an opportunity for attackers. It’s essential to keep all systems and associated software up to date with the latest security patches to mitigate these risks. But the fact that businesses are using an abundance of different platforms to manage and process their data, and the humans behind the business are using multiple devices to access it, increases the number of vulnerabilities that companies need to protect themselves against.
• Insider Threats
I’d love to tell you that the only threats to your business’ network security are strangers and attackers lying in wait. But there are also always going to be humans within your business, or competitors outside of it, who will be looking for any opportunity to take advantage of your weaknesses. Unhappy workers, angry ex-employees, humans with ties to your competitors, these are all internal threats that also need to be protected against. As much as you want to ensure that the humans within your business have access to the resources and tools that they need to work efficiently and effectively, you also need to ensure that they only have access to the information that they need to do their job, and no more than that.
• Human Error
Are you ready to hear a shocking statistic? According to research done by Stanford University, human error accounts for around 88% of data breaches.
And in this case, I’m not talking about the people in your business who are trying to do harm. I’m talking about the well-meaning humans who just don’t know any better, who make simple mistakes that should be easy to fix, or who don’t understand the risk that your company faces from something as an email being sent to the wrong person, or the wrong link being clicked.
Your humans are the first line of defence against network attacks, and it’s critical to ensure that they are not only trained in email security and cybersecurity best practices but also that those practices are made as straightforward as possible to encourage compliance.
• Shadow IT
Shadow IT, or the unapproved devices, apps, and services operating within your network, can be completely well-meaning. It could be that the humans within your business are just using devices that they haven’t told you about, or have found apps that help them to optimise their workflow. But anything that you aren’t aware of also has the potential to cause damage. An app that is exceptionally useful to a member of your Sales team could develop a vulnerability, for example. And because you don’t know that the app is being used, you also don’t know that it needs to be updated as a matter of urgency. And neither, in all likelihood, do they. This is just one example, but it’s how bypassing your company’s security measures can leave your network vulnerable. Identifying and managing shadow IT is an ongoing challenge.
• Third Parties
Businesses are more interconnected with third parties than ever. You’re integrating third-party APIs into your workflows, are using apps that you haven’t developed, but that you trust to enhance your operations. And this relationship can be wonderful, but it can also pose a risk to your business if you’re not careful about the third parties that you trust. Every third-party solution that you incorporate into your operations has the potential to extend networks and vulnerabilities if the API is not effectively managed. This makes it essential to enforce strict security policies across all parties that interact with your data.
How Can Businesses Protect Themselves Against Network Security Threats In 2024 And Beyond?
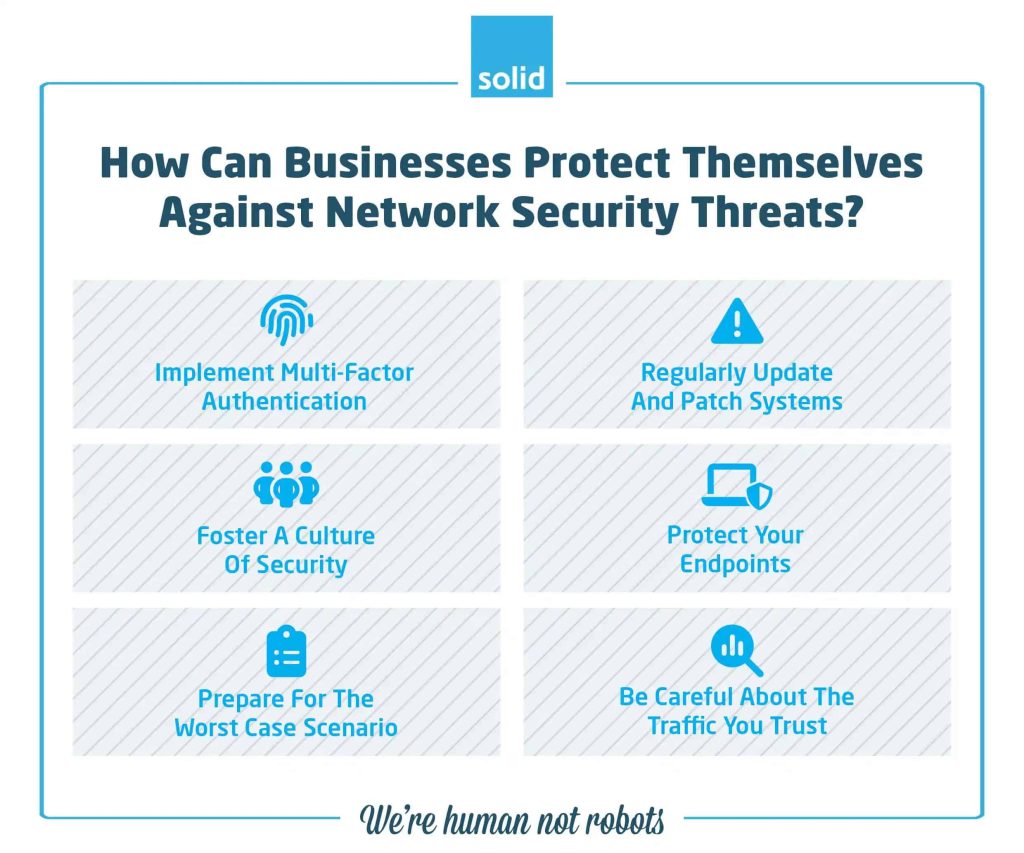
The rise of sophisticated threats means that businesses need to adopt equally sophisticated strategies to protect themselves. Here are some high-level approaches to network security:
• Implement Multi-Factor Authentication
Multi-factor authentication, or MFA, adds an extra layer of security to your network by requiring two or more passwords or verification methods to gain access to resources or data. Authentication methods can include passwords, verification codes which get sent to a cellphone or email address, biometrics like fingerprints or facial recognition, or physical tokens like key fobs.
• Regularly Update And Patch Systems
Keeping all software and hardware up to date with the latest security patches is essential in preventing exploitation of known vulnerabilities. Make it common practices for your IT team, and even the humans within your business, to install patches and updates as soon as they become available to reduce the risk of zero-day exploits.
• Foster A Culture Of Security
Education is key to adoption. If the humans behind your business have a thorough understanding of the threats that you face, and their role in preventing them, then they will be better equipped to recognise and counter any potential attacks, and are less likely to fall victim to human error.
• Protect Your Endpoints
Whether it’s the desktop computers that are based in your offices, or the cellphones, laptops and tablets that the humans in your business are using to connect to your network, you need to make sure that all endpoints and devices are as secure as possible, and are compliant with your network policies. This is also why businesses around the world are adopting Bring Your Own Device (BYOD) policies to ensure that even when their humans are using their personal devices to access business data, they are still secured from vulnerabilities.
• Prepare For The Worst Case Scenario
Hope for the best, but prepare for the worst. That’s a concept that most businesses should be adopting in this modern, digital age. Making sure that you have an incident response plan and a disaster recovery plan in place can be the difference between an attack crippling your business, or being little more than an inconvenience.
• Be Careful About The Traffic You Trust
Trust is earned. And when it comes to your network security, a Zero Trust model is the best approach to take. It assumes that every attempt to access your network is a potential threat and requires verification, regardless of where the request originates from. While a Zero Trust model may take more work to manage, it is the most secure approach to take when it comes to protecting your systems.
How Can You Set Up A Network Security Checklist, And What Should It Include?
Now that you have a better understanding of what network security involves, the threats that your business faces, and the techniques that you should be taking to secure your network against those threats, the next step is going to be setting up your network security checklist.
Why Do You Need A Network Security Checklist?
I’ve given you a few guidelines of what you can do to protect your network against attack, so why is it that you should also have a network security checklist in place? Well, a checklist is a roadmap that guides you through the process of securing your network from the ground up. It ensures that no vital aspect of your systems’ security is overlooked, providing a comprehensive approach to protecting your business.
What Should Be Included In Your Network Security Checklist?
An effective network security checklist should cover all aspects of your network infrastructure. Here are the key areas you should focus on:
Firewall Security
Firewall security acts as your network’s first line of defence, scrutinising incoming and outgoing traffic to deter unauthorised access. It’s essential for safeguarding your data and maintaining the integrity of your network infrastructure. Steps that you can include on your network security checklist include:
- Restricting unauthorised access
- Port blocking
- IP blocking
- Create an update and maintenance schedule as part of your security policies
Intrusion Detection And Prevention
Intrusion Detection and Prevention systems (IDPS) are critical for identifying and mitigating threats in real-time, ensuring your network’s security is proactive rather than reactive. Here are a few checklist items that you can tick off:
- Monitor network traffic
- Configure your signature and anomaly detection
- Set up alerts for suspicious behaviour
- Have an incident response plan in place for addressing any attempted attacks
Securing Your Wireless Networks
WiFi networks are often the most vulnerable part of a business’s network. A few points that you can include in your network security checklist for keeping them safe are:
- Encrypting data during transfer
- Using strong passwords
- Regularly updating wireless firmware
Identity And Access Management
Implement and regularly update access controls to ensure that only authorised users can access specific data or parts of your network, and that access rights are promptly revoked when humans leave your business, when roles change, or when they are simply no longer needed. Steps that you can take to prioritise Identity and Access Management (IAM) include:
- Putting strong password policies in place
- Implementing MFA across any apps need access to business data
- Setup group access permissions
- Regularly review and update user permissions
Data Protection And Encryption
Protecting sensitive information is paramount in today’s digital age. Encryption serves as a critical layer of defence, ensuring data remains secure, whether at rest or in transit, but there are other steps that you should include in your network security checklist as well:
- Set up data classification criteria based on sensitivity
- Apply strict security measures to critical data classifications
- Ensure that data is encrypted both at rest and during migration or transfer
- Setup automated cloud backups for important data
Endpoint Protection
Endpoint protection is crucial in safeguarding devices like desktops, laptops, and cellphones, and reducing the risk of them being exploited by malicious attacks. Some points that you can include in your network security checklist to protect the endpoints that your users have access to are:
- Put endpoint security software like Microsoft Intune in place
- Configure a Cloud Access Security Broker (CASB) to manage device patches and updates
- Conduct regular training on personal cyber hygiene practices
Network Security Policies
Developing and enforcing clear policies for network security can see the humans in your business gaining a greater understanding of their role in protecting your company. Policies that you may want to incorporate into your checklist include:
- Password policy
- Access-control policy
- BYOD policy
- App policy
- Information security policy
Regular IT Audits
It’s all too easy to put procedures in place and forget about them. But it’s critical to ensure that you’re constantly reviewing and improving your network security and ensuring that your business is as protected as possible. This means regularly reviewing your IT infrastructure and policies (like with a Solid Systems Review) to make sure that they’re in line with current and future best practices. Some areas to include in your audit involve:
- Conducting regular vulnerability scans
- Performing penetration testing
- Reviewing and assessing your systems and infrastructure
- Regularly reviewing and revising your policies
- Conducting regular security training with your teams
The Value Of Finding The Right Technology Partner For Your Business
Navigating the complex world of network security requires expertise. Expertise that many businesses out there either don’t have available to them, or want to put to use furthering their business, rather than looking over their shoulder. This is why it’s critical for businesses in today’s modern world to choose the right technology partner.
Working with the right managed IT services provider, or the right IT outsourcing partner can give your business access to the skills and resources that you need to develop and maintain an effective security strategy. But how do you know that you’ve found the right technology partner for your business?
At Solid Systems, we have spent the past two decades gaining a deep understanding of our clients’ unique network security needs, and helping them to stay ahead of threats, implement the latest security measures, and respond rapidly and effectively to security incidents. Our exceptionally human IT support goes beyond troubleshooting, but extends to finding the right technology and cybersecurity solutions to meet your needs, and putting strategic technology roadmaps in place to implement new services in the right way to enhance your operations and boost your overall security posture.
We don’t see network security as a one-time fix, but as an ongoing process that requires diligence, attention to detail, and a willingness to adapt to the changing landscape of cyber threats. By following the comprehensive network security checklist outlined in this guide, and partnering with Solid Systems as your technology guides, you can be confident that your business’s protection is as robust as it needs to be, both for today, for the challenges that lie ahead in 2024, and beyond.
Frequently Asked Questions
The three fundamental network security measures include using strong, unique passwords for all accounts and services, implementing firewalls to monitor and control incoming and outgoing network traffic based on predetermined security rules, and regularly updating and patching software to protect against known vulnerabilities and threats.
Popular Searches
- IT Company in Midrand
- What is Cyber Threat Protection
- Preventing Cyber Attacks
- Network Access Control
- Disaster Recovery
- IT Company in Gauteng
- Preventing Cyber Attacks
- IT Support in Sandton
- Ways To Protect Business Against IoT Cyber Attacks
- IT Support in Centurion
- Cyber Security Awareness
- IT Company in Durban
- Azure Backup and Recovery
- IT Company in Pretoria
- IT Trends
- Advantages of Outsourcing IT Services
- Cloud Computing and Cloud Infrastructure
- IT Company in Polokwane
- Benefits of Network Monitoring





